Essential Guide: Managing Trusted Root Certificates in Windows
Table of Contents
Frequently, update errors occur, revealing absent root certificates such as error 0x800b010a. Should you have encountered this error code, let’s delve into the nature of these trusted root certificates and the techniques to administer them on Windows PCs.
When inactive, these certificates impede other domain users from configuring their unique set. It becomes crucial to incorporate or administer these certificates in such scenarios.
Understanding Trusted Root Certificates in Windows
Trusted Root Certificates form an integral part of the public key infrastructure (PKI) within Windows. Their primary responsibility lies in safeguarding digital communications, spanning web browsing, email exchanges, and various online activities. They play a pivotal role in establishing trust and security in the digital sphere.
Acquiring and Installing a Trusted Root Certificate
Before initiating the management or inclusion of these certificates, it is imperative to download and install them initially. To obtain Trusted Root Certificates, launch your default web browser and navigate to the local certification server. You can explore Microsoft’s page to install these certificates via PowerShell.
Note: It is crucial to employ the same certificate of authority for generating both server and optionally, client certificates.
Upon visiting the official site, select and download a CA certificate, certificate chain, or CRL link, as required. Choose the appropriate certificate of authority from the list and opt for the Base 64 Encoding method. Subsequently, select the Download CA certificate link, and when prompted, choose the Open option to save the certificate.
When the certificate window opens, opt for Install Certificate…. This prompts the Certificate Import wizard. Proceed by selecting Next. When prompted for the Certificate Store, select Place all certificates in the following store and choose the Trusted Root Certification Authorities store.
Follow the on-screen instructions to finalize the installation process. Once successfully installed, select Finish.
Now that the certificates are installed on your PC, refer to the subsequent sections on how to add or manage them within the Microsoft Management Console.
Incorporating Trusted Root Certificates in Windows
Before managing any trusted root certificates, let’s grasp the process of adding such certificates on Windows. Here’s the sequence:
Step 1: Press Windows + X and select Run from the available options.
Step 2: Type ‘mmc’ in the text field and press OK. Authorize opening the Microsoft Management Console by selecting Yes when prompted by the UAC window.
Step 3: Navigate to File, and choose Add/Remove Snap-in. Alternatively, press Ctrl + M to access the Add or Remove Snap-ins window.
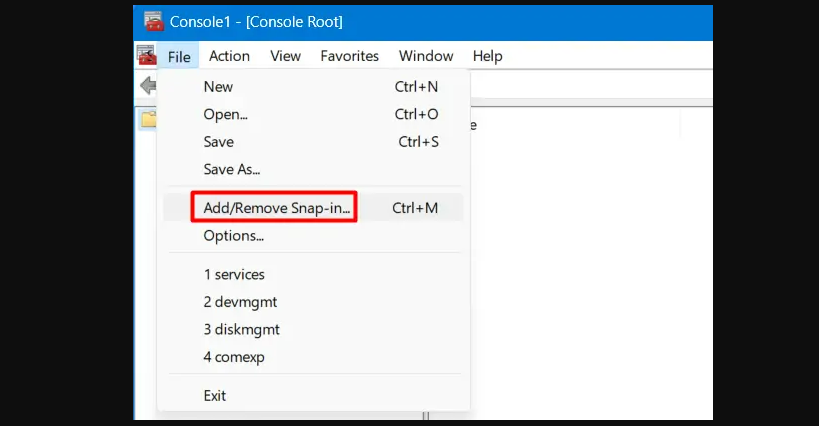
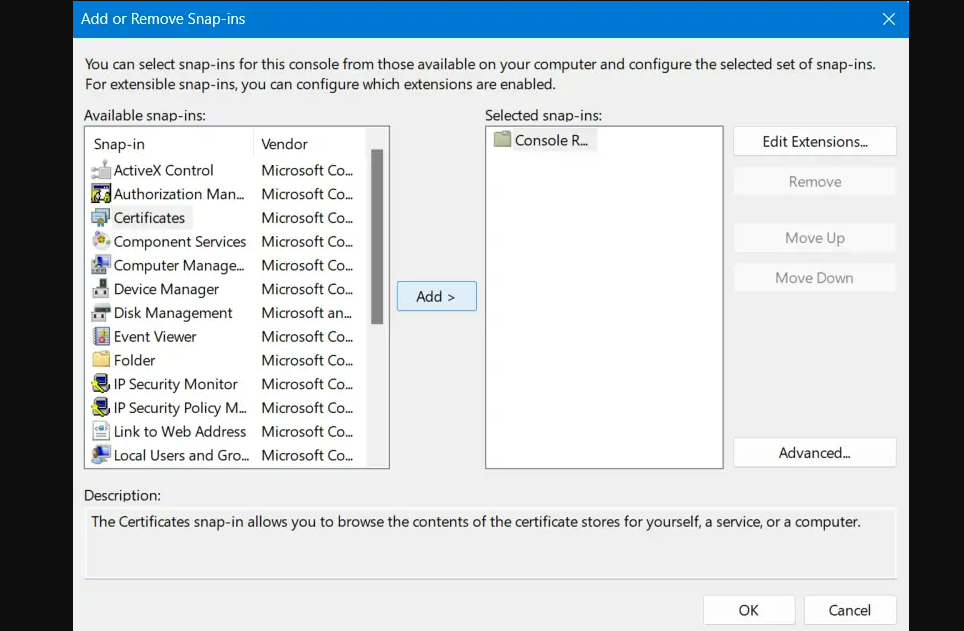
Step 4: Scroll to Certificates within the Available Snap-ins, click once on it, and hit Add.
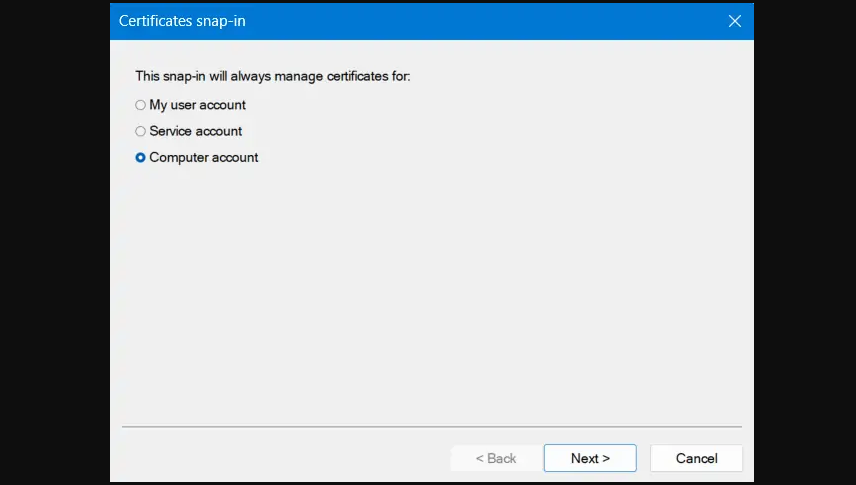
Step 5: The certificates snap-in window appears. Select the radio button adjacent to the Computer account and click Next.
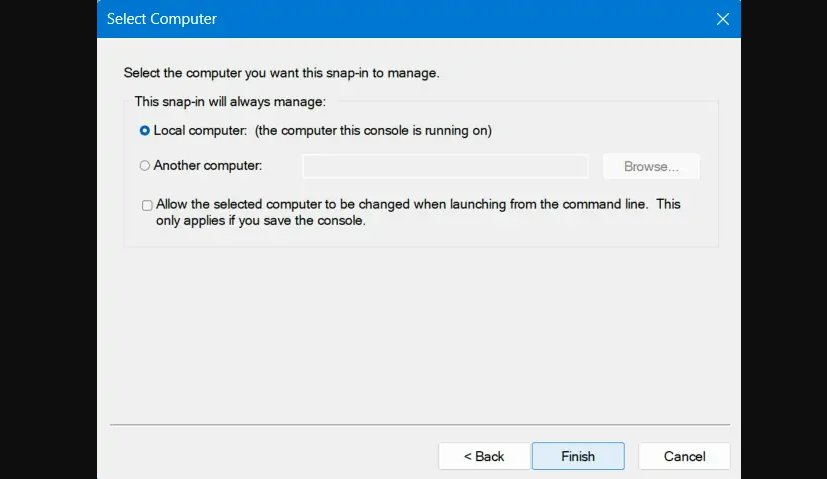
Step 6: Enable the Local Computer radio button, and then select Finish.
Step 7: “Certificates (Local Computer)” is now added under the Console Root inside the Microsoft Management Console.
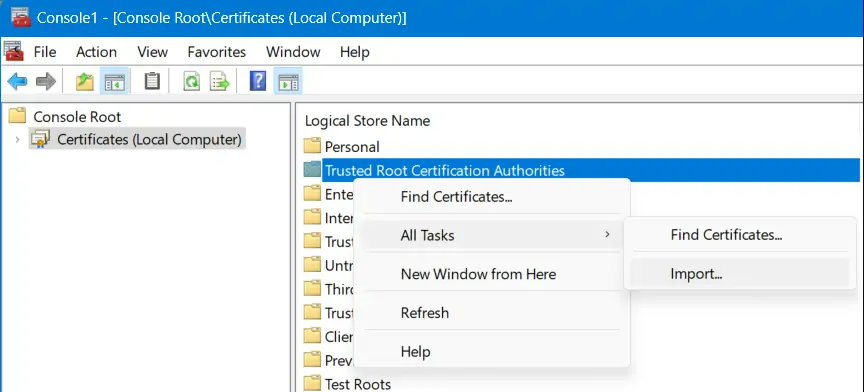
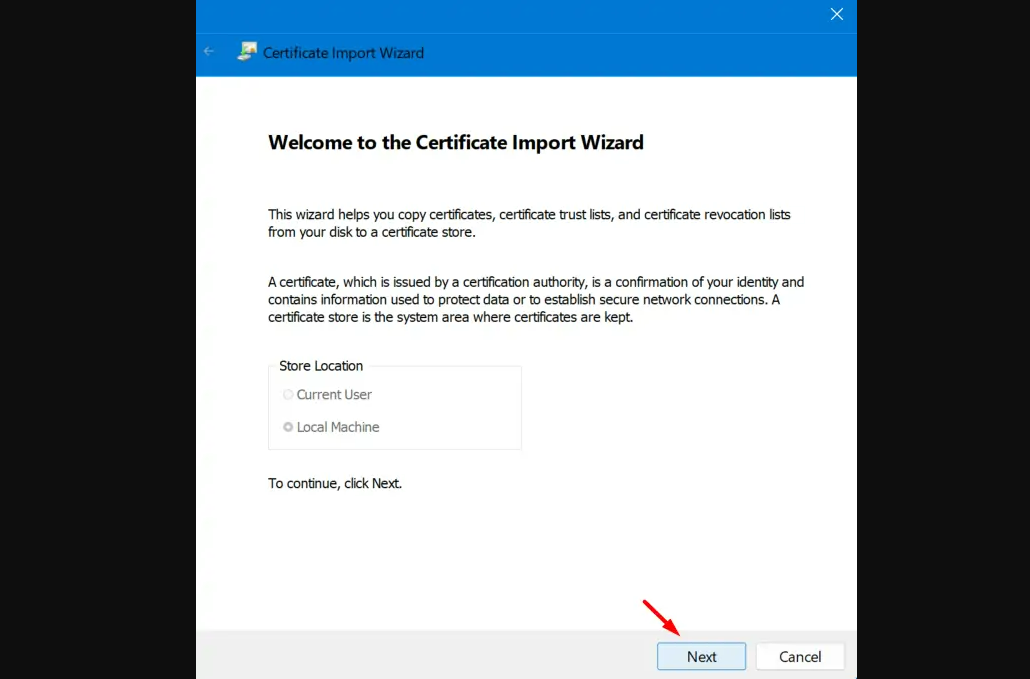
Step 8: On the Welcome to the Certificate Import Wizard, click Next.
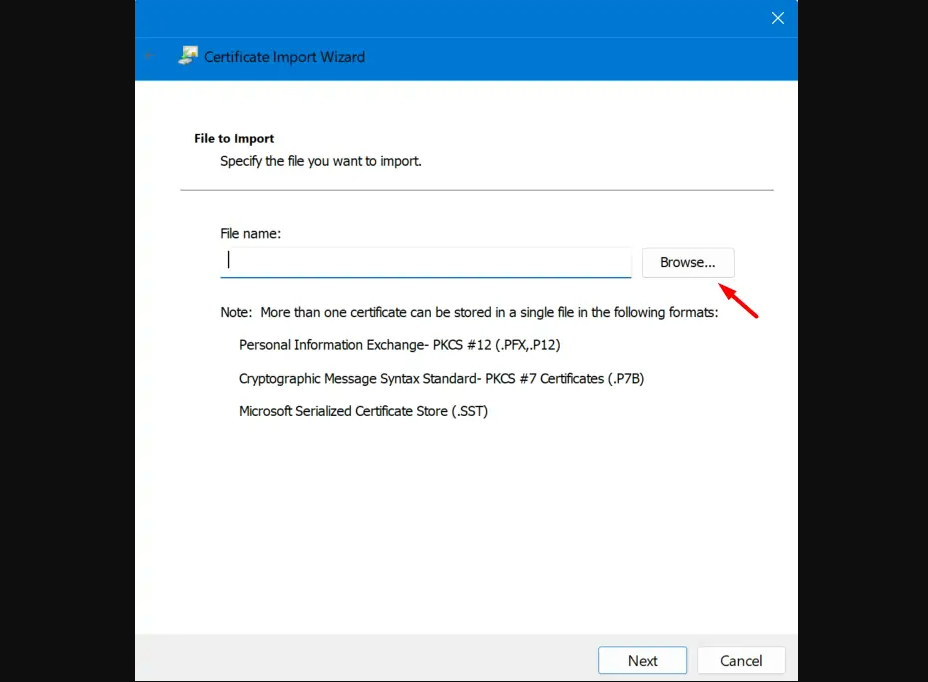
Step 9: Browse to the folder containing your trusted root certificates.
Follow the on-screen instructions to complete adding Certificates to MMC.
Managing Trusted Root Certificates
Now that you’ve learned to add a trusted root certificate, let’s navigate the steps to manage such certificates within the Microsoft Management Console.
Step 1: Return to the File menu and choose Add/Remove Snap-in.
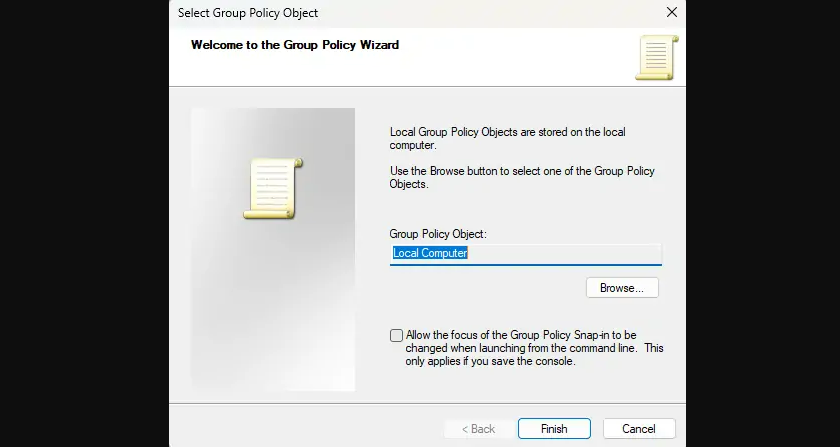
Step 2: This time, select Group Policy Object Editor under Available Snap-in.
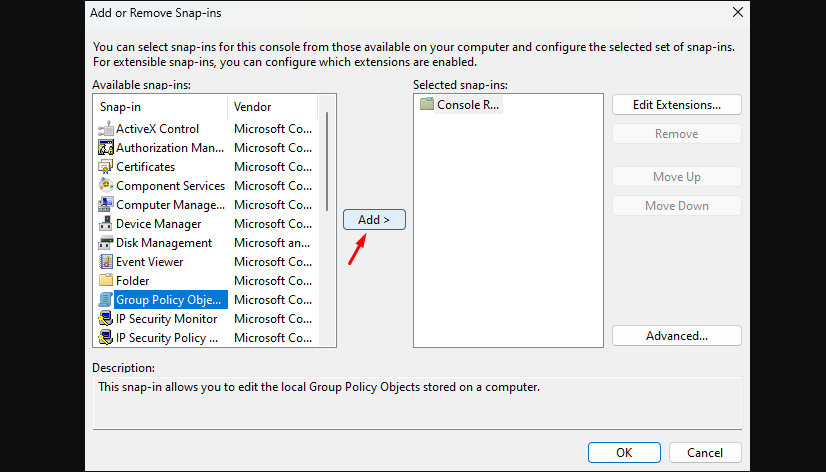
Step 3: Specify ‘Local Computer‘ under the Group Policy Object, check the tickbox, and click Finish.
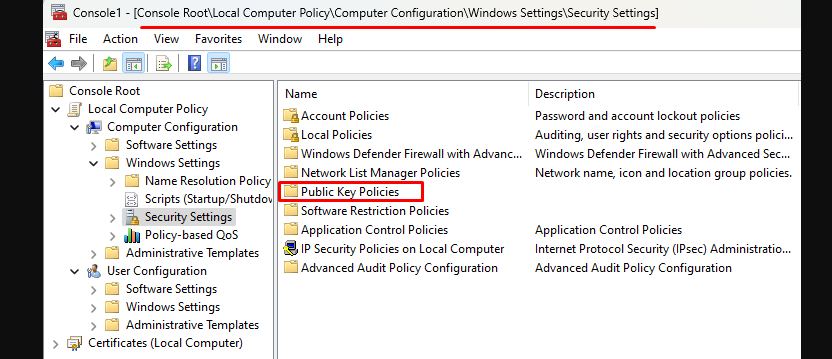
Step 4: Navigate through the MMC Console tree to the following path: Local Computer Policy > Computer Configuration > Windows Settings > Security Settings
Step 5: Locate and double-click on Public Key Policies.
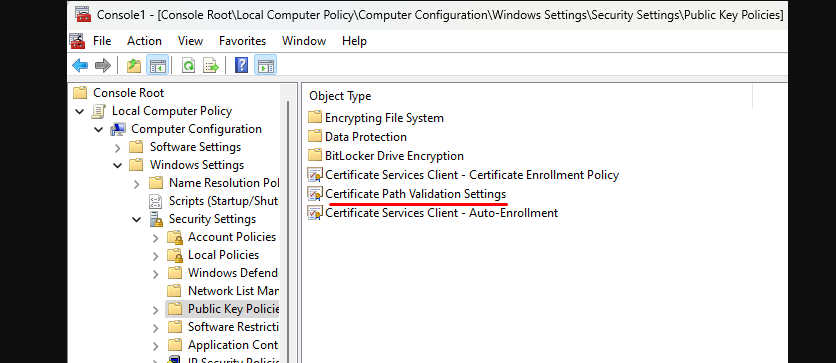
Step 6: Upon expansion, double-click on Certificate Path Validation Settings and select the Stores tab.
Step 7: Enable the tickbox to Define these policy settings and then enable both checkboxes under Per user certificates stores.
Step 8: Scroll to Root certificate stores and select the radio button next to “Third-Party Root CAs and Enterprise Root CAs (recommended).“
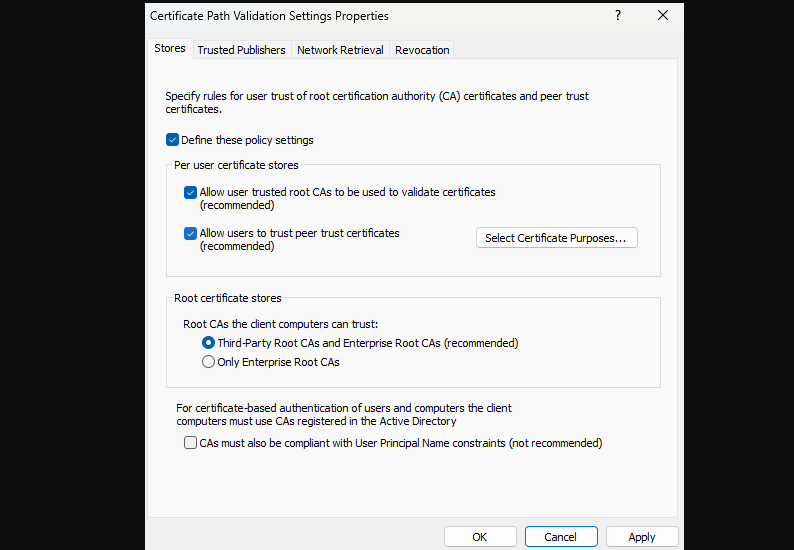
Step 9: Finally, click Apply and then OK to confirm the recent changes.
Once you have applied the alterations, it’s crucial to verify and ensure the changes have been successfully implemented within the system.
To verify the changes:
- Reboot your Windows PC to allow the alterations to take effect fully.
- Upon restarting, launch your web browser and perform routine online activities to check for any improvements in connectivity and security.
Concluding Remarks
Managing trusted root certificates in Windows is an essential aspect of maintaining the security and reliability of your digital operations. By comprehending the functionality and following the outlined steps, users can confidently add, install, and manage these certificates within the Windows environment.
Final Thoughts
Securing digital communications through trusted root certificates is pivotal in safeguarding against potential security vulnerabilities. Understanding their significance and effectively managing these certificates contributes significantly to a secure digital ecosystem.
Why are Trusted Root Certificates important?
Trusted Root Certificates establish trust in digital communication, ensuring security and authenticity.
Can I manage certificates without using MMC?
While MMC provides a user-friendly interface, certificates can also be managed via command-line tools like PowerShell.
Are there risks in mishandling root certificates?
Mishandling certificates can compromise the security of digital communications, potentially leading to security breaches.
Is it necessary to regularly update Trusted Root Certificates?
Yes, regular updates are essential to ensure the security and validity of certificates in the system.
Can I delete expired root certificates?
It’s recommended to remove expired certificates to maintain the system’s integrity and security.


